
MS Exchange servers under siege from at least 10 APT groups
On 2021-03-02, Microsoft released out-of-band patches for Microsoft Exchange Server 2013, 2016 and 2019 - on-premise versions only. These security updates fixed a pre-authentication remote code execution (RCE) vulnerability chain (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065) that allows an attacker to take over any reachable Exchange server, without even knowing any valid account credentials. We have already detected webshells on more than 5,000 email servers as of the time of writing, and according to public sources, several important organizations, such as the European Banking Authority, suffered from this attack.
These vulnerabilities were first discovered by Orange Tsai, a well-known vulnerability researcher, who reported them to Microsoft on 2021-01-05. However, according to a blogpost by Volexity, in-the-wild exploitation had already started on 2021-01-03. Thus, if these dates are correct, the vulnerabilities were either independently discovered by two different vulnerability research teams or that information about the vulnerabilities was somehow obtained by a malicious entity. Microsoft also published a blogpost about the early activity of Hafnium.
Exploitation statistics
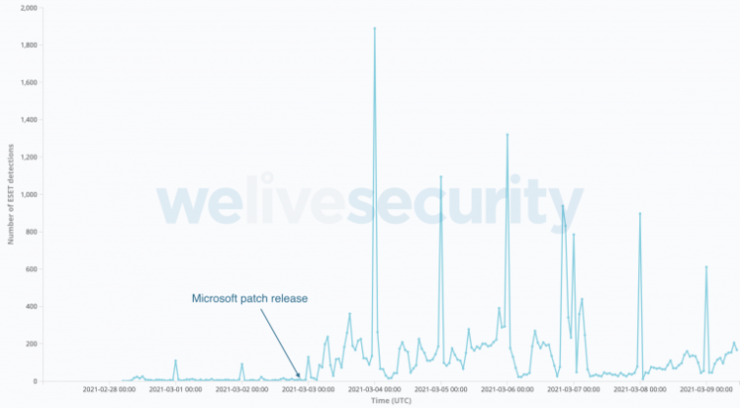
For the past few days, ESET researchers have been monitoring closely the number of webshell detections for these exploits. At the date of publication, we had observed more than 5,000 unique servers in over 115 countries where webshells were flagged. These numbers utilize ESET telemetry and are (obviously) not complete. The figure below illustrates these detections before and after the patch from Microsoft.
Summary
Our ongoing research shows that not only Hafnium has been using the recent RCE vulnerability in Exchange, but that multiple APTs have access to the exploit, and some even did so prior to the patch release. It is still unclear how the distribution of the exploit happened, but it is inevitable that more and more threat actors, including ransomware operators, will have access to it sooner or later.
It is now clearly beyond prime time to patch all Exchange servers as soon as possible (see Microsoft guidance and apply special care in following the steps in the “About installation of these updates” section). Even those not directly exposed to the internet should be patched because an attacker with low, or unprivileged, access to your LAN can trivially exploit these vulnerabilities to raise their privileges while compromising an internal (and probably more sensitive) Exchange server, and then move laterally from it.
In case of compromise, one should remove webshells, change credentials and investigate for any additional malicious activity.
Call us today if you have an on-premise Exchange server and want to check if you are vulnerable too.
Source: https://www.welivesecurity.com/2021/03/10/exchange-servers-under-siege-10-apt-groups/
